Introduction
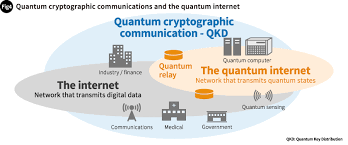
The advent of the quantum internet represents a paradigm shift in secure communication, with Quantum Key Distribution (QKD) emerging as a revolutionary technique. Unlike classical encryption methods, QKD leverages the principles of quantum mechanics to enable the exchange of cryptographic keys in a way that is theoretically immune to eavesdropping. In this article, we delve into the concept of the quantum internet and explore the groundbreaking role of Quantum Key Distribution.
Quantum Internet Basics
The quantum internet harnesses the principles of quantum mechanics, specifically the phenomena of superposition and entanglement, to enable secure communication beyond the capabilities of classical networks. Quantum bits or qubits, in a superposition of states, form the basis for quantum communication protocols. This quantum advantage allows for the creation of communication channels that offer enhanced security through the unique properties of quantum particles.
The Need for Quantum Key Distribution
Classical cryptographic methods rely on mathematical algorithms and the complexity of computational problems for security. However, the advent of quantum computers poses a potential threat to these systems. Quantum computers, when they become powerful enough, could easily crack widely-used encryption methods. QKD addresses this vulnerability by providing a fundamentally secure method for exchanging cryptographic keys, ensuring the confidentiality of digital communication.
The Uncertainty Principle in Quantum Key Distribution
Heisenberg’s Uncertainty Principle plays a crucial role in the security of QKD. This principle states that the more precisely one property of a particle is measured (e.g., its position), the less precisely the other property (e.g., its momentum) can be known. In the context of QKD, attempting to eavesdrop on quantum states inevitably introduces detectable perturbations, alerting users to potential security breaches.
Entanglement in Quantum Key Distribution
Entanglement is a quantum phenomenon where two or more particles become interconnected and the state of one particle instantaneously influences the state of the other, regardless of the distance between them. In QKD, entangled particles are used to create correlated quantum states for key distribution. Any attempt to intercept or measure the entangled particles disrupts the quantum states, providing a secure means of detecting eavesdropping.
Quantum Key Distribution Protocols
Several QKD protocols exist, each with its own approach to securing key distribution. Notable protocols include the BBM92 protocol, the Ekert protocol, and the B92 protocol. These protocols leverage various quantum properties, such as polarization states of photons, to establish secure cryptographic keys between communicating parties. The choice of protocol depends on factors like the quantum resources available and the specific requirements of the communication scenario.
Overcoming Quantum Channel Limitations
Quantum communication faces challenges, including the attenuation of quantum signals over long distances. Quantum repeaters, a crucial component in the development of the quantum internet, address this limitation. These repeaters extend the range of quantum communication by entangling particles across shorter segments of the communication channel, effectively creating a “quantum relay” system.
Quantum Internet Nodes and Hubs
The architecture of the quantum internet involves quantum nodes and hubs. Quantum nodes are endpoints that facilitate the exchange of quantum information, while quantum hubs serve as centralized points for connecting multiple nodes. This distributed architecture enhances the scalability and connectivity of the quantum internet, paving the way for a global quantum communication network.
Quantum-Safe Cryptography in the Classical Internet
While the quantum internet is in its early stages of development, the impending threat of quantum computers to classical cryptographic methods has led to the exploration of quantum-safe or post-quantum cryptography. This field aims to develop encryption algorithms that remain secure even in the face of quantum attacks, ensuring the long-term resilience of classical internet security.
Progress and Challenges in Quantum Key Distribution
Significant progress has been made in experimental demonstrations of QKD, with successful implementations over short distances. However, challenges persist in achieving long-distance, high-fidelity quantum communication. Overcoming issues like quantum signal loss, decoherence, and the development of practical quantum repeaters are active areas of research in the advancement of QKD.
Future Implications of Quantum Key Distribution
The successful implementation of Quantum Key Distribution holds profound implications for the future of secure communication. As the quantum internet matures, QKD is poised to play a pivotal role in safeguarding digital communication against potential threats posed by quantum computers. The development of a quantum communication infrastructure promises a new era of secure and private information exchange on a global scale.
Conclusion
The quantum internet, with Quantum Key Distribution at its core, represents a frontier in secure communication. By leveraging the principles of quantum mechanics, QKD offers a theoretically secure method for exchanging cryptographic keys, immune to potential threats posed by quantum computers. As research and development in quantum communication progress.